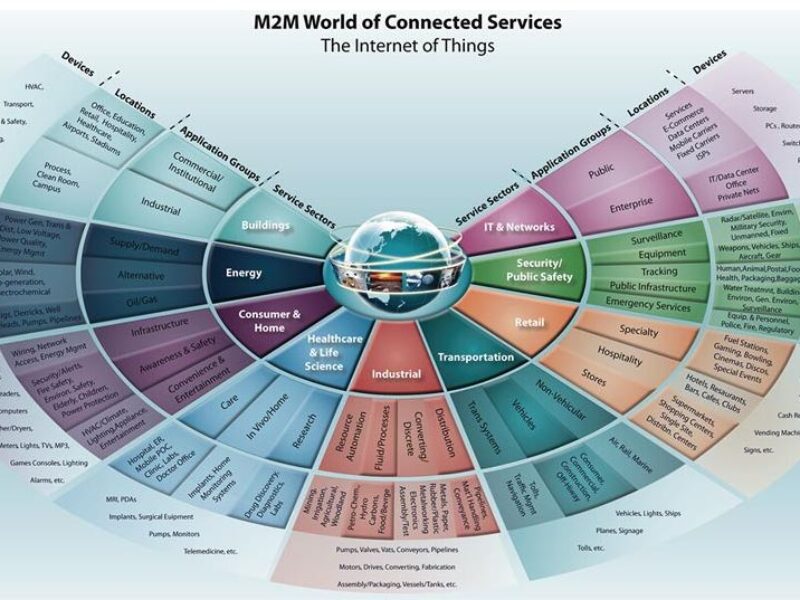
Excessive security will kill the Internet of Things
“There’s a certain amount of panic around the Internet of Things, that you need maximum security or not do it at all,” said Prof. Jon Howes, Technology Director at Cambridge-based Beecham Research and author of a new report on machine to machine (M2M) security. “The problem with M2M is the business model is always tight so as we put tighter and tighter security in place it will kill the business model and make it uneconomic.”
The key is the end-to-end architecture, he says. This is even more important with the recent launch of low cost microcontrollers such as Silicon Labs’ 49¢ Zero Gecko that include an AES encryption engine to support security applications.
In recent surveys, Beecham Research has identified end-to-end solution security as the leading concern for solution providers and for adopters of new M2M solutions. "Having analyzed the reality of security for M2M solutions, we have discovered emerging new principles and ways to make security both sufficient and economically viable. There is a profusion of new elements of security and new business models that will enable new markets," said Howes. "Engaged with correctly, this can at long last change security into a value producing capability instead of a resented cost."
This is not about just big players or vertical integration, he says. “It’s not necessarily big companies but people that know how to implement the end to end solution in the right environment,” he said. “Smart meters in the UK need a different architecture from smart meters in Germany, for example. A collection of partnerships is the way it’s going to go, and security risk and threat consultants will have a considerable role to play.” This will generate a $700m in security solutions for M2M by 2018 he predicts in "Issues and Business Opportunities in Security for M2M Solutions."
The report identifies the importance of right-sizing security for M2M solutions so as "not to kill the M2M patient" with an over-enthusiastic interpretation of the threats and risks involved. The report examines the widely varying degrees of security required for M2M solutions in different verticals and cautions a careful review of risk tolerance to avoid adopting overly strict security policies at the expense of the economic viability of the total solution.
www.beechamresearch.com
 If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News
If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News