Then European governments somehow faked their surprise and horror. “Why would you so comprehensively spy on your closest allies?” they asked candidly, industrial espionage being just a bonus.
Early November last year, I remember receiving some press releases from companies exhibiting at Paris-based event Milipol, about stealth fibre communications interception equipment and server-based snooping software, to be installed on telco’s racks (the press release didn’t say if they had to agree or not). This global event gathers all the who’s who in the tech world of law enforcement, crowd control, surveillance, and military equipment.
At the time, I just thought, “if it’s for sale, surely there is a well-documented market for it and undoubtedly it will be used by any state or company acquiring it”. Nearly every day, there was a new revelation in the newspapers about how comprehensive, how “unfair” the NSA’s surveillance strategy had become.
And you can bet that pretty much every country represented at Milipol was looking for similar solutions, only limited by their spending budget, either to spy on others or to closely control their own citizens or very wide encompassing “select groups of activists”.
This surveillance scandal definitely gave a boost to providers of data encryption solutions, since you could argue that well encrypted data is rendered useless for analysis. The marketing pitch is easy now that we know pretty much anyone of us is virtually spied upon, indiscriminately.
Security technologist Bruce Schneier, a regular contributor to The Guardian on secure communications, got early access to leaked NSA documents to help journalists clarify the technical implementations of data collection and sifting. His main conclusions regarding encrypted data, is that the NSA will circumvent state-of-the-art encryption by finding the weakest point in the communication chain, accessing the data at weakly protected spots before the hard encryption takes place.
Often these include the end-points, your mobile device or computer, running an easy to tamper operating system, possibly compromised software, and poorly chosen passwords. What’s more, the huge amounts of meta-data collected across social networks and any internet page you visit will give up as much about you as low-level social engineered phishing.
In his analysis, Schneier warns that large commercial encryption software can be assumed to have installed backdoors, and that being open, public-domain encryption solutions will less likely be perverted. You could use hidden services, such as Tor to anonymize yourself, but then the NSA will more specifically target any group of users trying to hide or encrypt their communications. The “air gap” as Schneier likes to call it – moving data from a non-connected computer to a connected one using an encrypted USB key – is pretty efficient, but then I suppose the next level of secrecy would simply be not to share your secrets or at least stop communicating them electronically.
A friend of mine who’s daily job in a state-funded lab is to crack secure chips and evaluate their protection level, told me that there is no such thing as a secure chip, it is just a matter of resources. So the so-called secure chips will just be winning the encryption race against poorly-funded hackers, that is, most low-level criminals.
The compromise is to find a good-enough level of security for the application to be secured, where the potential criminal gains would not compensate the cost of breaking it. Of course, that just won’t hold back state-funded hackers.
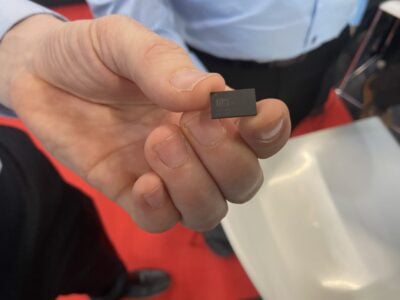
So the announcement of the Sectra Panthon 3 smartphone app for secure voice communication and text messaging, granted EU approval for the protection of EU classified information, somehow makes me smile. Yes, the end-to-end smartcard-based encryption (via a plug-in microSD-card) is probably very secure at least against most common interceptors, and since it is available as a service, the users can rely on all major public wireless networks.
They don’t have to manage encryption keys either. Now a PIN code is all that is needed to activate the added protection, boasts the press release. Hopefully you won’t choose 123456, ranking at the top of SplashData‘s "Worst Passwords of 2013".
Related articles:
Selective encryption said to cut wireless power
Solid-state drive features self-encryption for laptops and desktops
Cloud encryption software protects data itself rather than storage media
 If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News
If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News