New possibilities for smart-factory security
Intelligent production that automatically adapts to products or circumstances, providing convenient remote control and remote maintenance are poised to bring manufacturing to a new level in terms of quality, efficiency and flexibility. However, networking industrial installations and the consequent autonomous communication between ‘things’ also bring with it new risks. For instance, what happens if hackers or manipulated systems seize control of robots or industrial installations? In other words, how does a ‘thing’ know that the data or data selections it receives from another ‘thing’ are legitimate and that these system components are ‘who’ they say they are?
Three steps to security – Identification, authentication, authorization
IIoT issues can be addressed through the use of modern security solutions in classic IT, along with communication between human users. These solutions require identification, authentication and authorization here on the example of a user.
- Identification involves a user to log-in to reveal his/her identity – in doing so confirms that he/she is a specific user.
- The next step is authentication, i.e. verifying that the user is who they say they are. In order for this to occur, the user needs to identify themselves by means of a password/PIN and/or additional hardware-specific identification credentials, which can be a token, smart card or the like.For applications where security is mission critical, two-factor identification is needed comprising of elements such as a password/PIN in addition to a non-copyable means of validation such as face recognition or other biometrics tools.
- Once the user has been successfully identified, access is granted and usage rights provided with approved permissions (authorization).
The user could also be thought of as a (sub-) system in machine based processes.
Problems that arise in real life
Pure software-based solutions for installations requiring security (including production lines and industrial installations) do not provide adequate protection and can be easily copied and manipulated. Systems that communicate with each other via the internet or through IIoT gateways must, on one hand provide an identity that cannot be cloned, and on the other, have the ability to send and receive highly secure encrypted data. Such protection always requires a solution that is integrated into hardware, known as a security anchor.
Selecting the right security anchor for a given application can be done in any of a number of ways:
- by installing SIM cards (as is done with mobile phones);
- by soldering identifiable hardware components (Trusted Platform Module (TPM)) onto the relevant components;
- or through the use of processors that can be unambiguously identified via integrated elements (Trusted Execution Environment (TEE)).
Although all of these solutions provide levels of protection and have a number of pros and cons, under real conditions they are subject to certain limitations which need to be considered. One thing they all have in common is that they limit the flexibility of the solution provider, binding equipment manufacturers to certain producers, components and/or processors, and distribution channels in the technological development processes.
Flash memory using a “TPM” as the solution
One of the world’s leading providers of flash memory solutions and industrial storage media, Switzerland-based Swissbit, suggests a new solution – industrial flash memory cards with embedded security which functions as a Trusted Platform Module (TPM). This solution is advantageous for IIoT component and solution developers and can meet safety requirements as well as performing other functions.
Ideal for industrial applications
The advantages kick in during the integration phase, which becomes very simple for developers for a number of reasons:
- the memory interfaces are standardized;
- middleware for cryptographic operations is available;
- flash memories with TPM-functionality are available in various form factors including SD cards, micro SD cards and USB sticks.
This solution is based on flash memory modules, which for many years have been highly rated for use under industrial conditions – such as a much larger temperature range than consumer/commodity cards and a far superior product life-span and availability.

A smart combination – memory and security
Swissbit’s idea of combining a unique identifier with a standard data storage device is elegant by virtue of the fact that most IIoT components and systems already need memory for their data and operating systems.
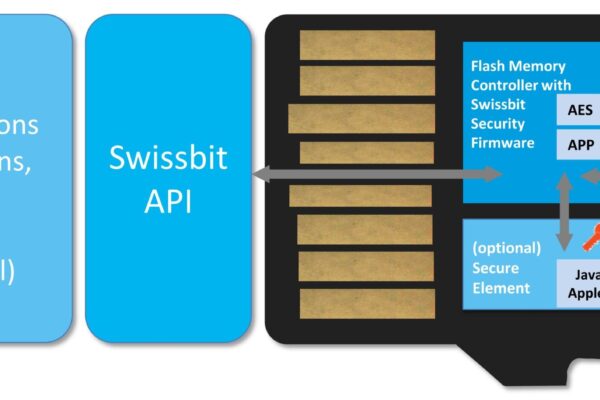
Swissbit secure memory cards, which are already widely used in big deployments for wiretapping-proof governmental mobile phones and police body cams, are mainly composed of a flash memory chip, a smart card and a controller. Their special firmware with integrated AES encryptor supports other application scenarios. The fact that Swissbit uses a crypto chips as security anchor means not only that communication is secure, but also that data can be securely encrypted. This in turn allows for Trusted Boot implementation and license monetarization. What’s more flash memory with an integrated encryptor can be used to encrypt a system’s data storage devices such as classic hard drives.
Retrofitting legacy systems?
One of the obstacles to establishing IIoT security is that older systems and components lack adequate protection. Now legacy systems and components that have USB or SD interfaces can be easily equipped with counterfeit-proof identities and can then be integrated into the existing security solution. Retrofitting continues to be a key issue as the life cycles of security solutions and industrial memory cards are remarkably similar. Similar to memory cards, security algorithms are subject to wear and tear. As such, the length and algorithm requirements continuous change to protect against increasingly sophisticated attacks. The ease of substitution makes the combination of storage and security an ideal combination.
Security for mobile use
Systems and installations used in smart factories of the future will no longer have specific operating elements and screens, but will instead be operated, monitored and maintained via mobile devices and tablets. The constant desire for mobilization and cost reduction ultimately shifts control to mobile devices and thus into low-trust environments beyond a physically protected facility. But what are the security implications for mobile access?

security applications.
With Swissbit’s solution, security using standard tablets and highly secure user authentication via secure microSD card is no problem. After logging on, users are reliably identified via a PIN which unlocks the secure authentication identifier which can never be copied. This is even possible through a PC via a USB stick. This allows users with the defined required permissions to securely access the relevant systems at any time.
Conclusions
Users who – with good reason – want secure processes such as encryption and two-factor identification in classic IT networks and on the Internet shouldn’t be satisfied with anything less than this in the IIoT.
When it comes to machines, robots or entire industrial installations that largely run autonomously based on sensor data and ‘make decisions,’ it must be ensured that these only process or deliver data when the relevant data-transferring systems are uniquely identified.
For this reason such systems need to be equipped with counterfeit-proof identities. This can be provided via flash memory solutions that use crypto chips as TPM. Apart from being highly flexible, they can be retrofitted and an be combined with other functions such as encryption and data protection.
There are many opportunities for such applications, particularly in areas where industrial flash memory cards are already used. In medical equipment the security of patient data can be improved, and manipulation can be avoided during metering. In tracking logistics, industrial terminals can be safeguarded from external attacks, and secure processes can be implemented with relative ease. Flash-Memory combined with high security provides a truly smart solution.
About the Author:
Hubertus Grobbel is head of the Swissbit AG security products department – www.swissbit.com
 If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News
If you enjoyed this article, you will like the following ones: don't miss them by subscribing to :
eeNews on Google News




